Introduction
To start with an enterprise often uses the Agile-DG (Agile Data Guard), or similar means, to protect itself from internal security threats related to internal staff. However, due to business reasons, the enterprise might face the situation where it needs to send important decrypted files to external business partners. In this case confidential business data in distributed files (DF) may become out of control. It is then necessary to solve the security management problem to ensure that confidential enterprise data is still in control, although being distributed. Agile-FD (Agile File Distribution) is a software product that provides a solution to this type problem.
By using the same powerful encryption engine as Agile-DG and its own high-strength encryption algorithms Agile FD provides a way to distributes encrypted but readable files and prevent leaks due to secondary transmission.Agile-FD solves the following problems:
1)Improve administrative efficiency and simplify the decryption process: First, users need to request decrypted binding and specify which files are to be distributed. Then management personnel within the enterprise decide, accordingly to predefined rules, whether to approve this request. If the request is approved, necessary operations will be executed on the FD server automatically. This greatly reduces the risk related to decryption operations performed on client side also takes away the tedious process of manual decryption operations.
2)Prevent secondary leaks due to illegal decryption of confidential files in external organizational units: When confidential files are sent to external organizational units the control is defined with attributes such as valid time period, maximum number of open operations etc. The external unit can only access the file using its specific browser plug-in, with specified restrictions. This way, secondary leaks from outside staff can be effectively prevented.
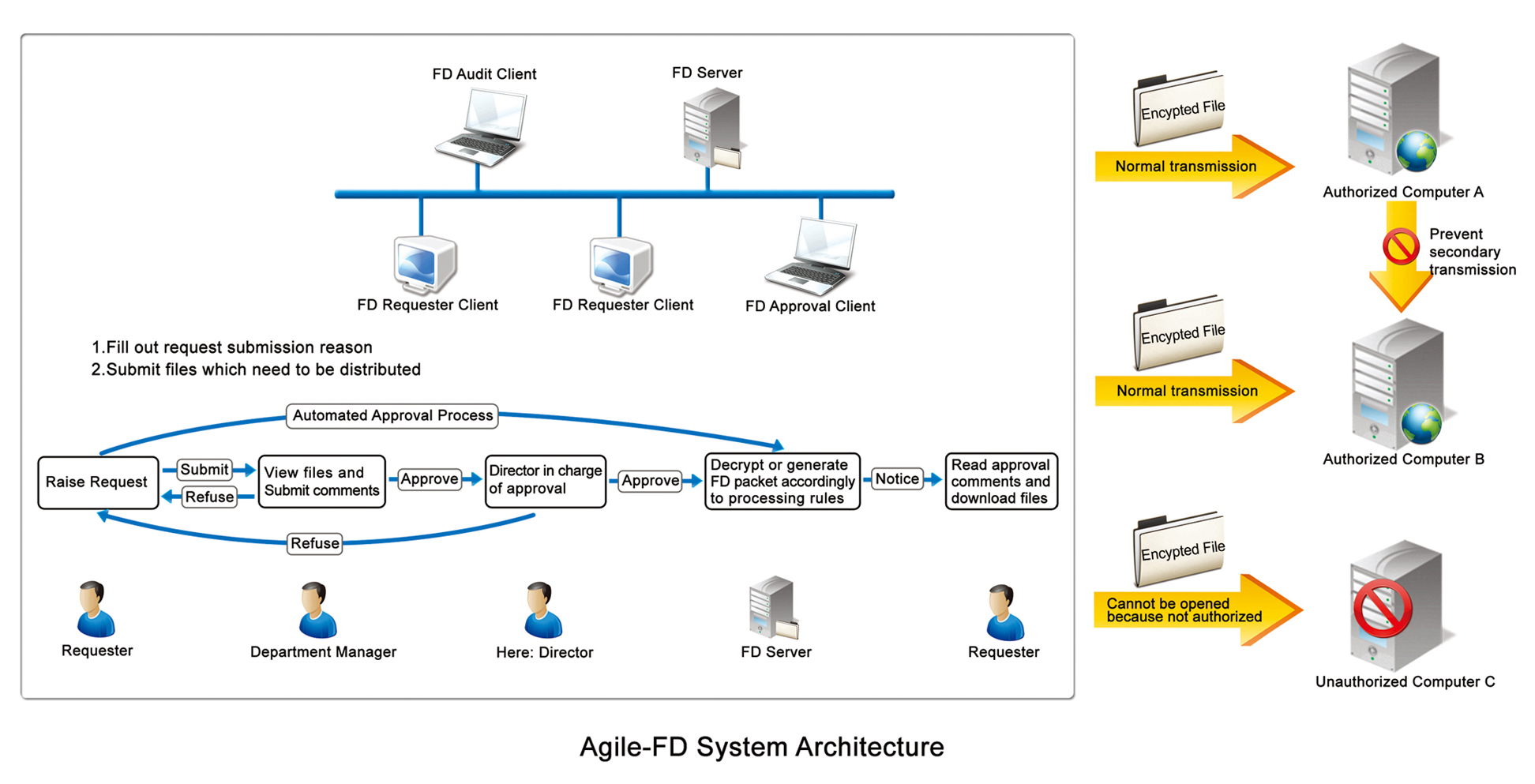
FD System Functions
Thanks to the Two-Tier B/S (Browser/Server) structure Agile-FD is easily and conveniently deployed. Only the server needs to be installed, not any client. The user access the Agile-FD Server through a web browser equipped with a plug-in, so maintenance is reduced compared to a solution based only on Agile-DG which requires the installation of a DG Client on each computer. FD Server provides different privileges to different users. Depending of their rights the users can enter various functional modules, for example the Raise Request Module, the Approval Module, the Audit Module. Agile-FD provides the following functions:
Approval Procedure for File Distribution: The FD approval process takes into account the organization’s existing approval procedures. First, the user raises a request to generate a distributed file. Then, involved approval staff examines and authorize the request on the server and the distributed file is generated accordingly to the restrictions. Finally, the server informs the requester or, depending of the rules, immediately transmits the files. If the requester is to transmit the files, he may do so within authorized limits.
External Computer Identification: The authorized distribution file can only be opened on a computer which has been installed with a relevant browser plug-in, generated by the manage client module on the FD server. Not only do the users need to send the authorized distribution files, they also need to provide browser plug-ins to their trusted partners.
File validity period and restricted number of open operations: The file distribution requester defines the valid time period, maximum number of open operations, whether operations such as modify, print etc are to be allowed for. If authorization limits are not respected the file becomes invalid for future use.
File Access Rights Control: When the distributed file is opened all operations should be constrained by authorization rules. For example, the distribution file cannot be modified, copied to another file, printed, captures of displayed screens are not permitted, etc. Even if the DF is allowed to be edited upon, it is still encrypted after this operation. Besides, “save as” operation is forbidden.
Creation of Distributed File on FD Server: If the distributed file creation request is approved the distributed file is automatically created in the background on the FD Server and then transferred to the requesters computer. A copy will always remain on the FD server.
Backup Distribution File: according to the authorization rules, the FD server will back up created distribution files on the FD server for future review
Organization Structure Definition: Agile FD maps user names on an Organization Structure defining companies, departments and registered user identifications. It assigns available modules for each user, authorizes various usage templates operations.
Manage User: The main utility of this function is to add user information in order to facilitate user identification for a requester when a file distribution request is to be made. The approver may also easily see whereabouts of the distributed file. The distribution browser plug-in is also generated in this module.
Process Definition: Process Definition Structure clarifies approval authorities and the process workflow definition with a simple model using “Persons” and “Rules”. Department Managers can select relevant users as approvers. Multi-level identification can be made.
Automatic Approval: If the request is to be approved accordingly to defined rules the FD Server may do so automatically, without manual intervention.
Delegated Approval: An approver may delegate to a trusted person the possibility to evaluate and approve a request.
Usage Templates: Usage Templates may be developed in line with different needs with regard to file distribution mode and approval procedures (reference to above mentioned process definition).
Log Management: This module provides all records related to requests and approvals. This includes information on requesters, distribution user information, distributed file information etc. Log reports in Excel can also be generated.
Browser plug-in generation: Accordingly to different levels of security requirements Agile FD can generate four kinds of browser plug-ins: 1 Direct mounting type, 2 Password authentication type, 3 Hardware binding type, 4 USB key binding type.
Prompt message: When the prompt message application is installed the approver can receive request related notifications in real time.
Audit: Users with audit rights can read records for requests and approvals, both previously executed records and records currently being processed.
Execution Environment Compatibility:
Server/Management Unit:Supported Operating Systems: Windows 2003/R2 series,2008/R2,2012
Software Environment: Internet Explorer 6.0 or above, Windows Installer 3.1, SQL Server2000 or above, IIS Service, NET Framework 2.0
Client Plug-in:
Supported OS:Windows 2000 series,XP series,2003 series,Vista series,7 series,8 series.
HW environment: Professional Server with minimum configuration Pentium IV 2.0 or higher level processor, RAM Memory>1 GB, Hard Disk >500 MB free space, Network Card >10/100M.
Antivirus Software Compatibility: There is no conflict with conventional antivirus software.


